Group and Granted Security Identities
Group and Granted Security Identities
The basic secured search scenario handles permissions well as long as the permission model only contains user security identities. However, secured enterprise systems typically also include user security identities in group security identities and granted security identities. This article describes these two types of security identities.
|
|
Note
To place the focus on item permission management, all examples in this article assume that the query made by the search page user matches the title of the desired items. |
Group Security Identities
Enterprise user management systems typically encourage including users in groups, especially when dealing with many users. Using groups can make permission attribution faster and more efficient since you can create a group security identity representing all users that have the same title or are members of the same team or department.
A group security identity represents the sum of all its member security identities. When a group is allowed or denied access to an item, all group members have the same permission.
All 114 employees working in the R&D Department at MyCompany should be able to access R&D_Roadmap_2017.pdf.
Therefore, in this item permission model, instead of marking one by one the 114 user security identities as allowed to access the item, you mark the R&D Department group security identity, rd@mycompany.com, as allowed.
The R&D_Roadmap_2017.pdf item permission model is therefore:
rd@mycompany.com: allowed
Rather than:
-
banderson@mycompany.com:allowed -
jbates@mycompany.com:allowed -
rcooke@mycompany.com:allowed -
sdonovan@mycompany.com:allowed -
etc.
Group security identities can also include other groups, or both groups and users.
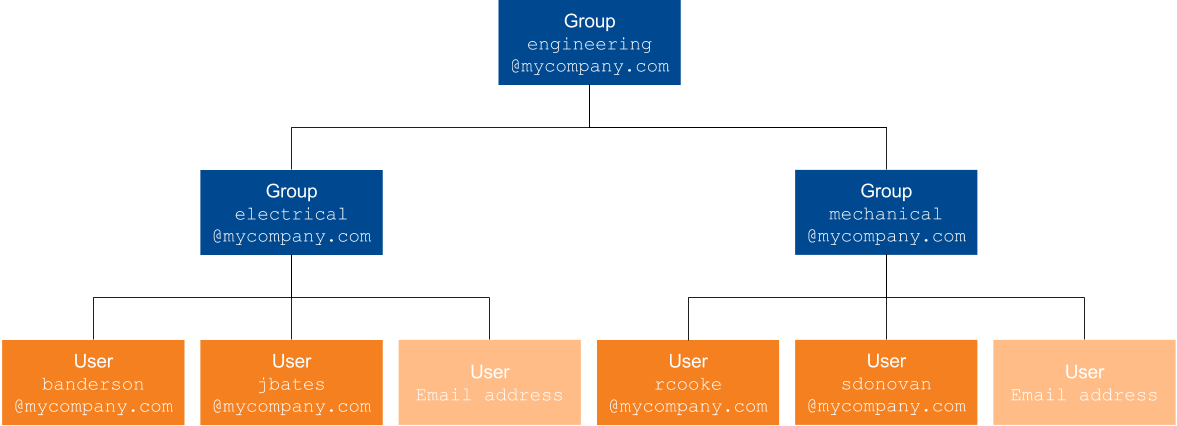
You base your group creation on your workplace department and team hierarchy. You therefore create the following group security identity hierarchy:
engineering@mycompany.com
-
electrical@mycompany.com-
banderson@mycompany.com -
jbates@mycompany.com -
etc.
-
-
mechanical@mycompany.com-
rcooke@mycompany.com -
sdonovan@mycompany.com -
etc.
-
engineering@mycompany.com is a group security identity that contains other groups, while the two other groups contain user security identities such as banderson@mycompany.com.
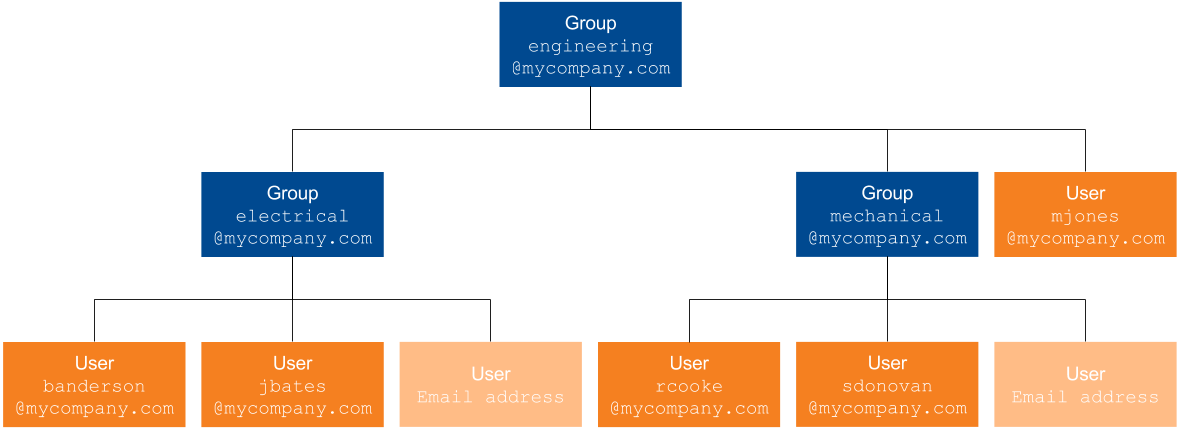
You want the company vice-president, Mark Jones, to be included in the engineering@mycompany.com group.
Your group security identities are therefore:
engineering@mycompany.com
-
electrical@mycompany.com-
banderson@mycompany.com -
jbates@mycompany.com -
etc.
-
-
mechanical@mycompany.com-
rcooke@mycompany.com -
sdonovan@mycompany.com -
etc.
-
-
mjones@mycompany.com
Granted Security Identities
Coveo handles granted security identities (formerly known as well-known groups) like groups when analyzing an item permission model. As a result, both of these security identity types can be marked as allowed or denied access to the item in place of a list of individual security identities.
|
|
Notes
|
Granted security identities differ from group security identities in that it’s impossible to retrieve a list of their members, because often such a list doesn’t exist. The secured enterprise system automatically knows whether it should grant a certain security identity to a user depending on the users' characteristics, so it doesn’t store an exhaustive list of who is granted which security identity. This list is required because the index needs it to filter search results and it must therefore be obtained otherwise. Since it can retrieve the granted identities of all users using the security identity provider, the Coveo security identity cache can easily determine which users are linked to which granted identity (see Security Identity Relationships and Security Identity Cache and Provider). Coveo therefore handles granted security identities as smoothly as group security identities.
Jive/AllRegisteredUsers is a typical Jive granted security identity.
It represents all users that have a Jive account, as opposed to anonymous users, who didn’t log in and aren’t identified.
Your Coveo-powered search page is used through your website by both your employees and your customers.
Employees can authenticate on the search page while your customers, who access the search page without logging in, are anonymous users (see Public Items and Anonymous Users).
Your employees should be able to access the Corporate Christmas Party video, but not your customers, because the crawler marked Jive/AllRegisteredUsers as a security identity allowed to access the video, and customers don’t have a Jive account.
What’s next?
A group or a granted security identity is usually related to at least another security identity (see Security Identity Relationships).