Permission Levels
Permission Levels
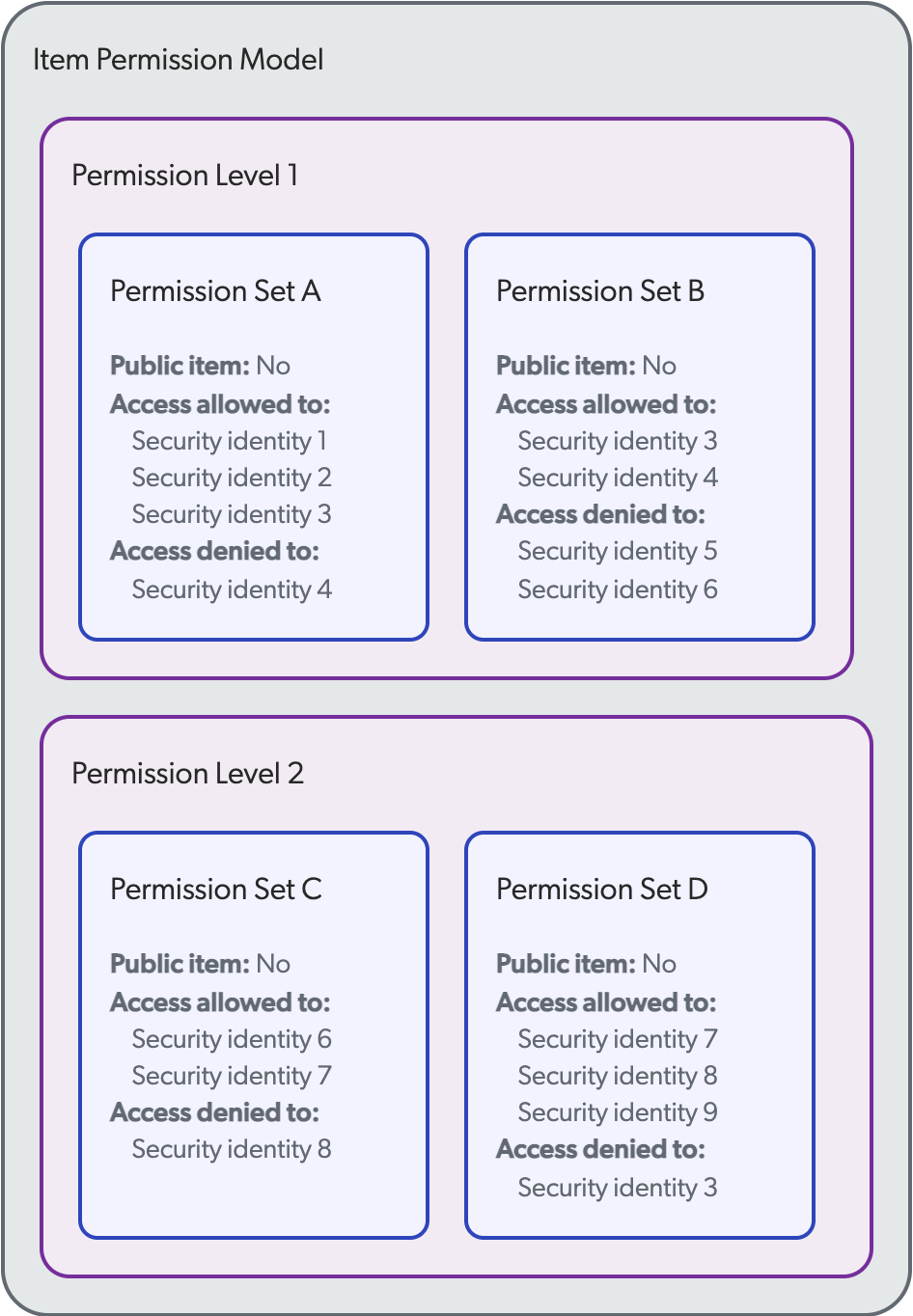
In some secured enterprise systems, permission models consist of more than one permission set. However, in some permission models, some permission sets prevail over others. In such cases, the permission model for each item consists of two or more permission levels, which in turn consist of one or more permission sets.
A separate article covers how the Coveo Platform manages permission sets. Secured items have a permission model listing the security identities that are respectively allowed and denied access to this item.
 The typical Coveo secured search example illustrates how permissions are managed when the item permission model consists of a single permission set within a single permission level.
This article covers how permission models are resolved when they contain more than one permission level.
The typical Coveo secured search example illustrates how permissions are managed when the item permission model consists of a single permission set within a single permission level.
This article covers how permission models are resolved when they contain more than one permission level.
Permission levels are analyzed one at a time. So, if the first one is satisfied and the user is allowed or denied access to the item, the other levels are ignored. If a user isn’t specified in the first permission level, the analysis is inconclusive. The second level must therefore be analyzed and so on, until a level is satisfied. Then, whether the user is allowed or denied access to the item by the subsequent permission levels is irrelevant.
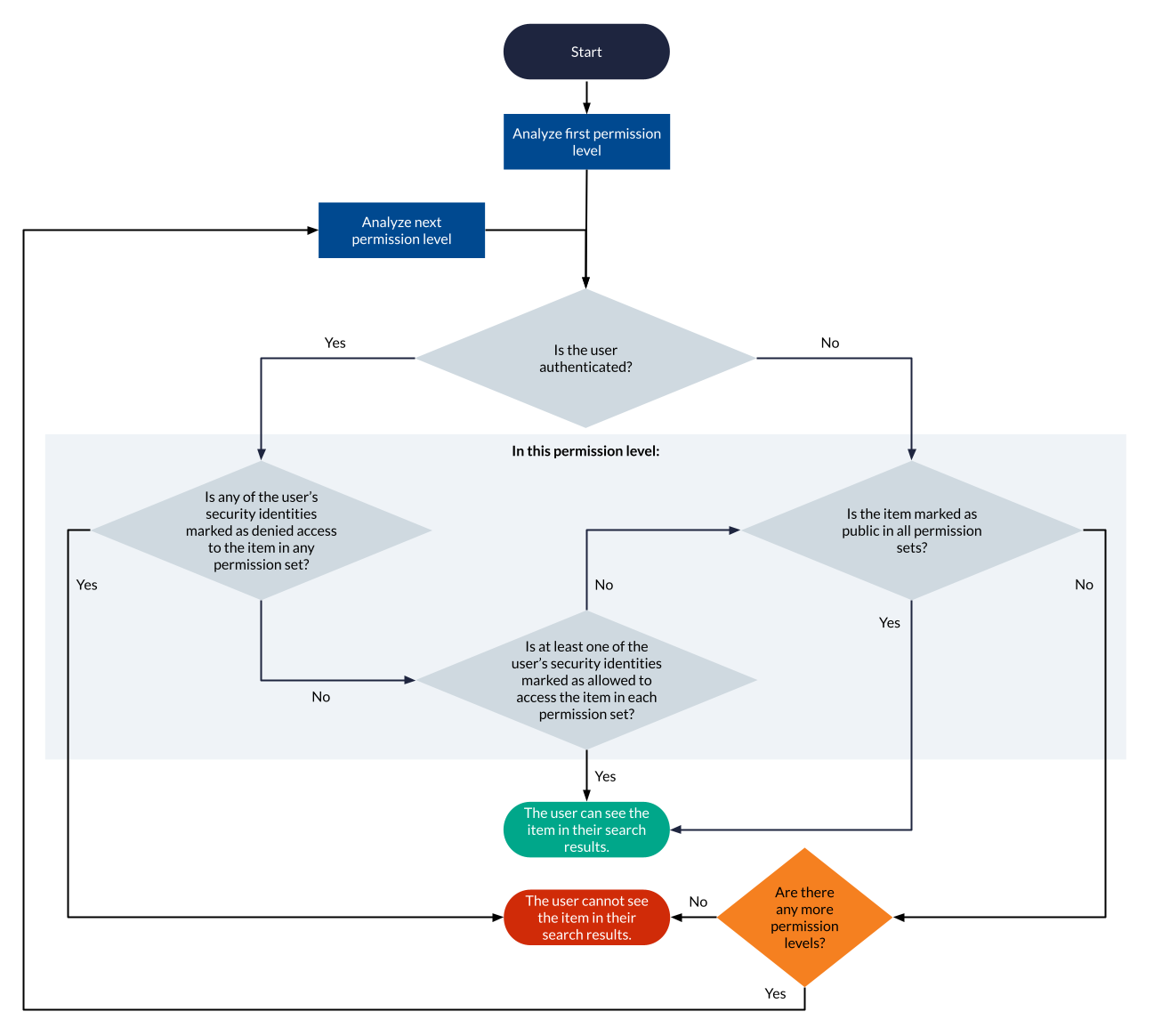
The following flowchart summarizes the permission sets analysis process executed for each item matching a query to determine whether the item should appear in the user’s search results. The process is the same as that involved in the typical Coveo secured search scenario, except that there are several permission sets and levels to analyze rather than a single one.
Example
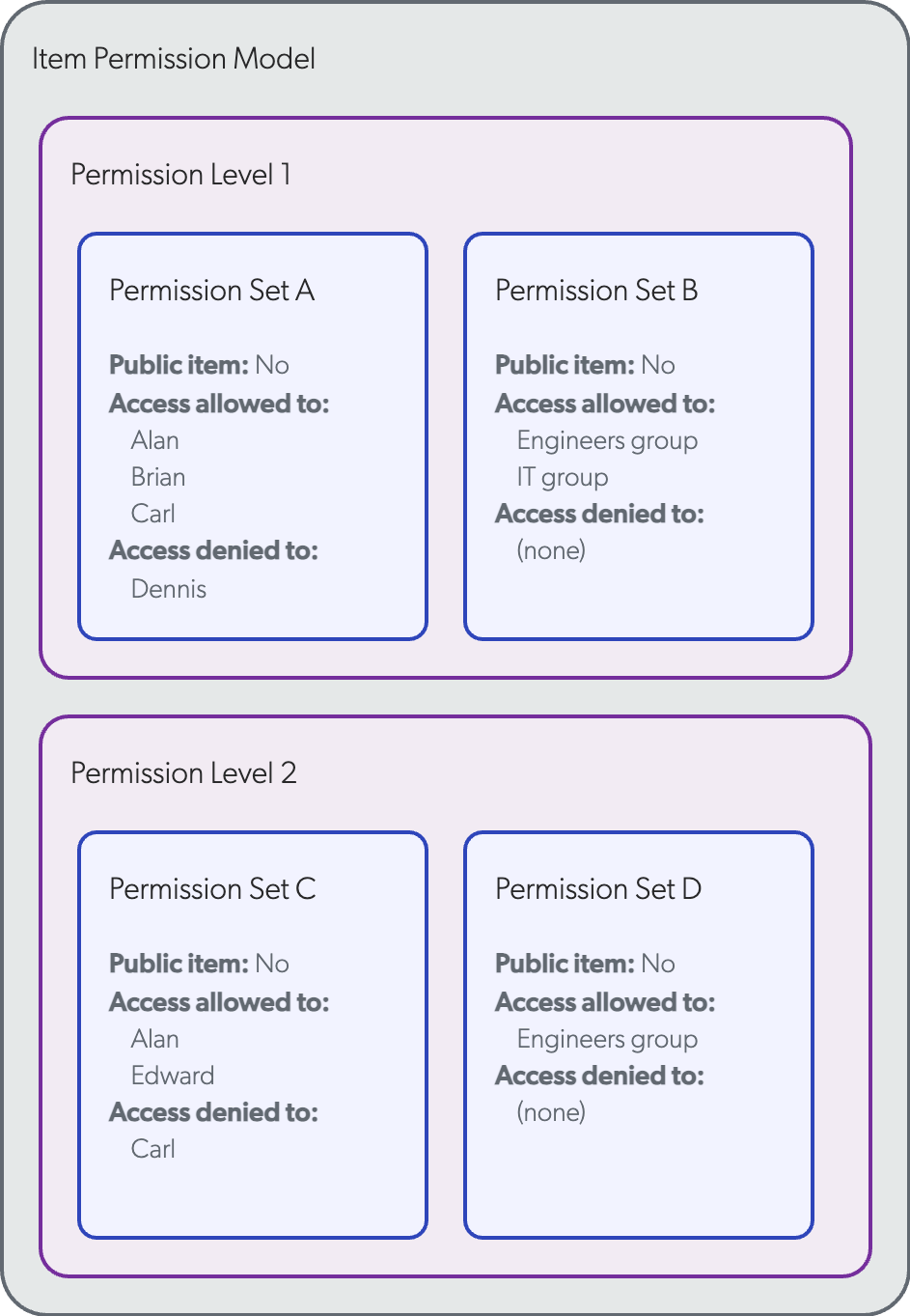
A private, secured item has the following permission model:
-
Permission Level 1 (highest level, analyzed first)
-
Permission Set A
-
Public item: No
-
Allowed:
-
Alan
-
Brian
-
Carl
-
-
Denied:
-
Dennis
-
-
-
Permission Set B
-
Public item: No
-
Allowed:
-
Group Engineers
-
Group IT
-
-
-
-
Permission Level 2
-
Permission Set C
-
Public item: No
-
Allowed:
-
Alan
-
Edward
-
-
Denied:
-
Carl
-
-
-
Permission Set D
-
Public item: No
-
Allowed: Group Engineers
-
-
Alan, Carl, Edward are members of the Engineers group. Brian and Dennis aren’t members of any group.
Alan: allowed access by Permission Level 1
In Permission Level 1, no permission set explicitly denies Alan access to the item. However, Alan is marked as allowed access in Permission Set A and, since he’s part of the Engineers group, he’s also allowed access by Permission Set B. Since all permission sets of Permission Level 1 allow Alan to access the item, he can see it in his search results.
Brian: all permission levels are inconclusive
Just like for Alan, no permission set explicitly denies Brian access to the item. He’s allowed to access the item by Permission Set A, but he’s not part of neither the Engineers nor the IT group allowed by Permission Set B. The item not being marked as public in all its permission sets, it is considered private, and therefore Permission Level 1 is inconclusive. Permission Level 2 must be analyzed to determine whether Brian can access the item.
In Permission Level 2, no permission set explicitly denies Brian access to the item. However, Brian is not specified as allowed to access the item in neither Permission Set C nor D. The item being considered private, Permission Level 2 is also inconclusive. There is no more permission to analyze to determine Brian’s access status, so he’s denied access to the item by default. He can’t see the item in his search results.
Carl: Permission Level 1 prevails over Level 2
The analysis of Permission Level 1 allows Carl to access the item, just like Alan. Carl is explicitly denied access to the item in Permission Level 2, but since Permission Level 1 was satisfied, it prevails and Permission Level 2 is ignored. Carl is therefore allowed to access the item and can see it in his search results.
Dennis: denied access by Permission Level 1
In Permission Level 1, Dennis is denied access to the item by Permission Set A. He therefore can’t see the item in his search results.
Edward: allowed access by Permission Level 2
Just like for Brian, Permission Level 1 is inconclusive regarding Edward’s status. In Permission Level 2, no permission set explicitly denies Edward access to the item. Moreover, Edward is allowed access by both permission sets, as he is a member of the Engineers group. He’s therefore allowed to access the item and can see it in his search results.
Effective permissions
The item effective permissions, that is, the global permissions that apply to the item once its permission model has been resolved, are the following:
-
Allowed users: Alan, Carl, Edward
-
Denied users: Brian, Dennis