Permission Sets
Permission Sets
The typical Coveo secured search example covers how permissions are managed for sources based on some of the connectors supported by Coveo. As mentioned before, a secured item has a permission model listing the security identities that are respectively allowed and denied access to this item.
However, in certain secured enterprise systems, permission models consist in more than one permission set, which each include:
-
A list of security identities allowed to access the item
-
A list of security identities that are denied access to the item
-
Whether the item is accessible to everyone (see Public Items and Anonymous Users)
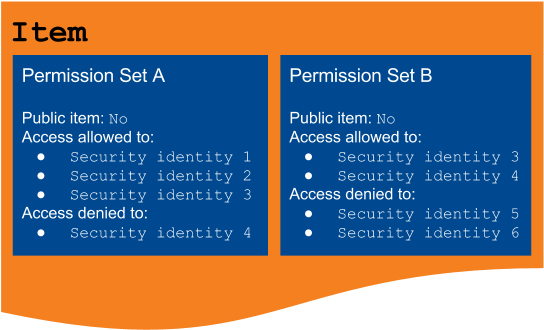
The typical Coveo secured search example illustrates how permissions are managed when the item permission model consists of a single permission set. This article covers how permission models are resolved when they contain more than one permission set.
|
|
Note
To place the focus on item permission management, all examples in this article assume that the query made by the search page user matches the title of the desired items. |
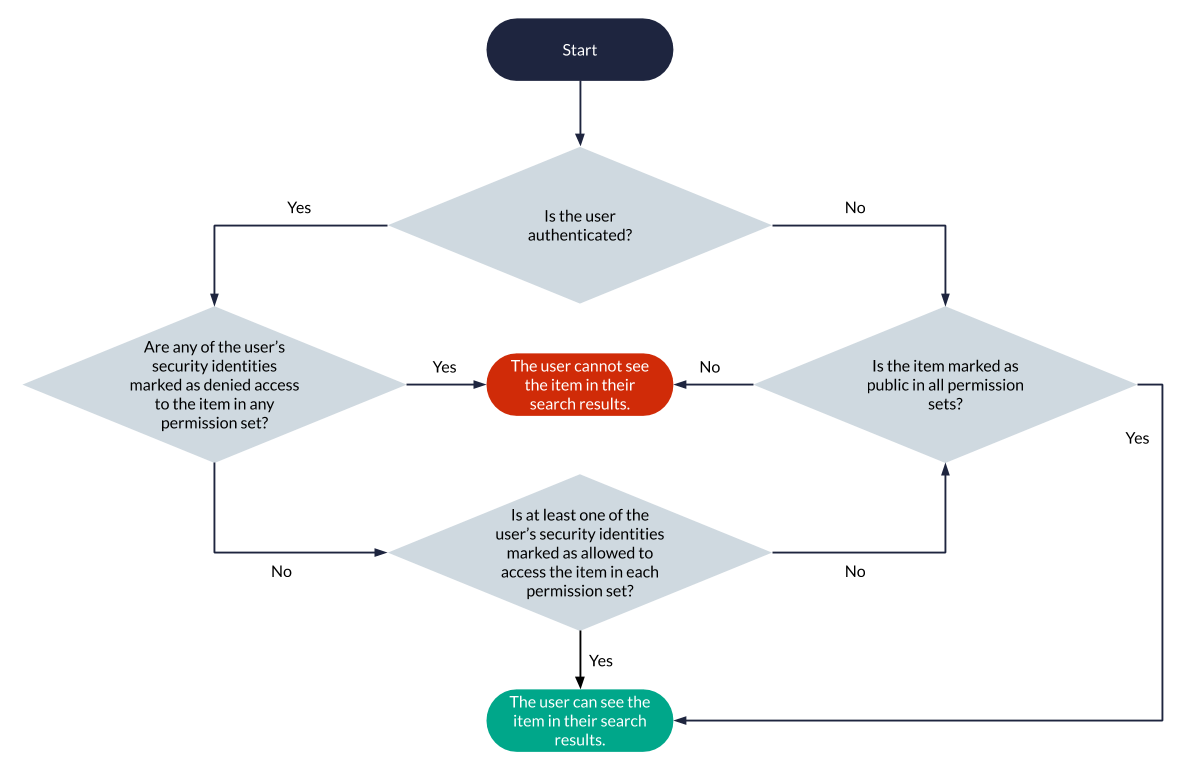
As covered before, when an item permission model consists of a single permission set, at least one of the querying user’s security identities must be marked as allowed to access the item, and none must be denied access to this item for it to be displayed in the user’s search results. When a permission model includes several permission sets, at least one of the querying user’s security identities must be marked as allowed in each permission set, and none must be denied access to this item in any of the permission sets. In other words, all permission sets must be individually satisfied for the item to be displayed in the user’s search results.
Moreover, the other permission rules specified in the previous articles apply to each permission set as well. For example, if one of the user’s security identities isn’t specified in a permission set, the user is considered as denied for this set, and therefore denied access to the item (see Unspecified Security Identities). Similarly, if all permission sets specify the item as public, the item is available to all users, except those who have at least one of their security identities marked as denied access to the item in at least one permission set (see Public Items and Anonymous Users and Denial Prevalence).
The following flowchart summarizes the permission set analysis process executed for each item matching a query to determine whether the item should appear in the querying user’s search results. The process is the same as that involved in the typical Coveo secured search scenario, except that there are several permission sets involved rather than a single one.
MyCompany has chosen to index a secured enterprise system to make its content searchable via a Coveo-powered search page.
This secured enterprise system contains items of various confidentiality levels. To enforce the confidentiality rules and levels, each item has one or more access conditions, which determine who can access the item. For a user to be allowed to access an item, they must fulfill all access conditions.
In this secured system, John Smith and Barbara Allen are members of the Administrators group (see Group and Granted Security Identities), while John Smith and Mary Davis are members of the Security Advisors group.
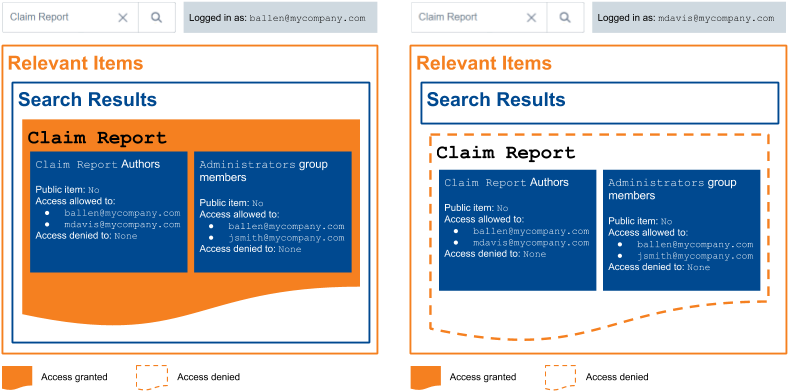
Item Claim Report has the following access conditions:
-
User must be an author of
Claim Report -
User must be a member of
Administratorsgroup
Barbara Allen and Mary Davis are authors of Claim Report and fulfill the first access condition.
However, Mary Davis isn’t a member of the Administrators group, and therefore only Barbara Allen meets both access requirements.
Only she can access Claim Report.
Similarly to Mary Davis, John Smith, as a member of Administrators, fulfills the second condition, but not the first one, and can’t access Claim Report.
In other words, in this case, each item access condition corresponds to a permission set. When a user meets the condition, they’re marked as allowed in the corresponding permission set.
The item effective permission model, that is, the global permission model that applies to Claim Report once all permission sets have been compared, is the following:
-
Allowed user: Barbara Allen
-
Denied users: Mary Davis and John Smith
Allowed users are those that meet all access requirements, while denied users are either unspecified users or users that only meet some of the requirements (see Unspecified Security Identities).
In the same enterprise system, item Account Data has the following access conditions:
-
User must be a member of
Administratorsgroup -
User must be a member of
Security Advisorsgroup
As mentioned above, only John Smith is a member of both of these groups.
Since he fulfills both conditions, he is allowed to access Account Data.
Mary Davis and Barbara Allen, however, can’t access this item because they don’t meet both requirements.
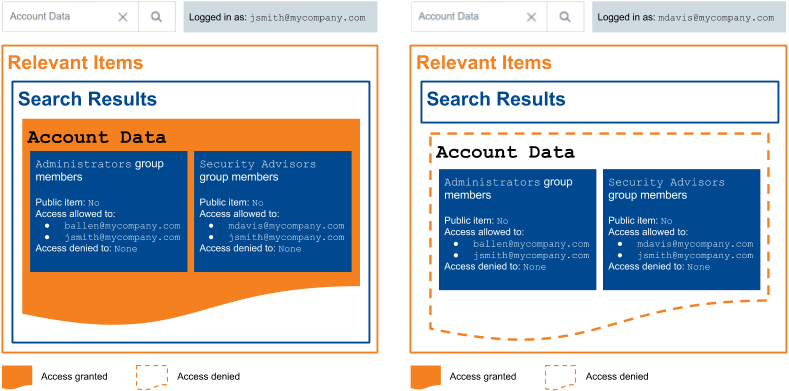
The Account Data effective permission model is therefore the following:
-
Allowed user: John Smith
-
Denied users: Mary Davis and Barbara Allen
What’s Next?
Some permission sets may prevail over some others (see Permission Levels).