Authorize Coveo to access your Google content
Authorize Coveo to access your Google content
To authorize Coveo to access your Google content, you must perform a Google Workspace (formerly G Suite) domain-wide delegation of authority after creating a Google Cloud Console project and service account.
Authorize your service account client ID
-
Access the Google Workspace Admin Console with a super administrator account. Super administrator privileges are required for domain-wide delegation, which you’ll configure later on.
-
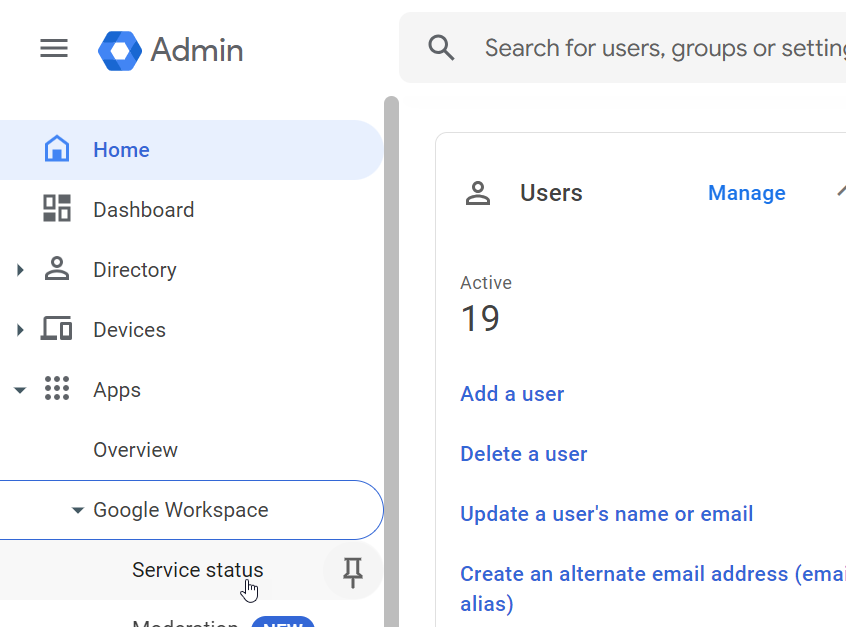
In the main menu, select Apps > Google Workspace > Service status.
-
In the Services list, ensure that the status for Drive and Docs is set to On for everyone.
-
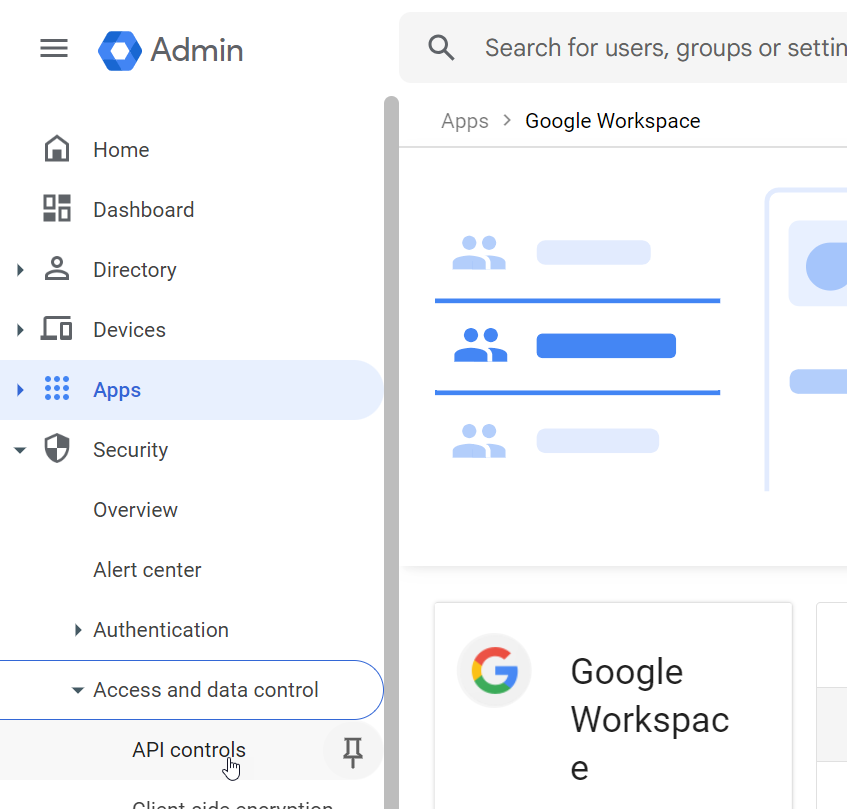
In the main menu, select Security > Access and data control > API controls.
-
In the Domain wide delegation pane, click Manage Domain Wide Delegation.
-
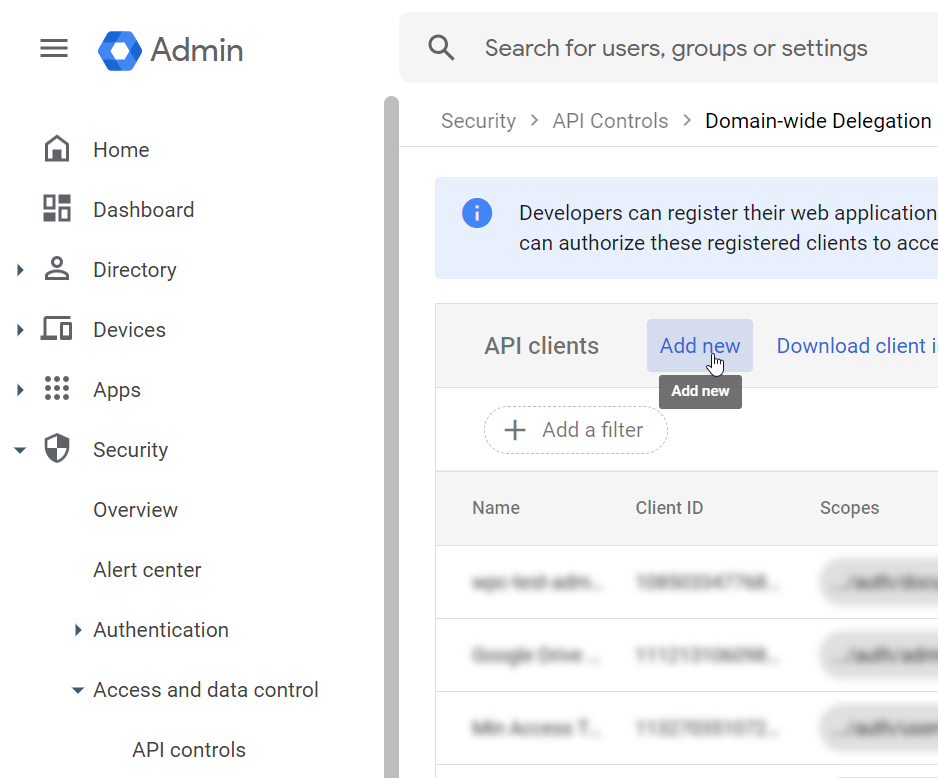
Click Add new.
-
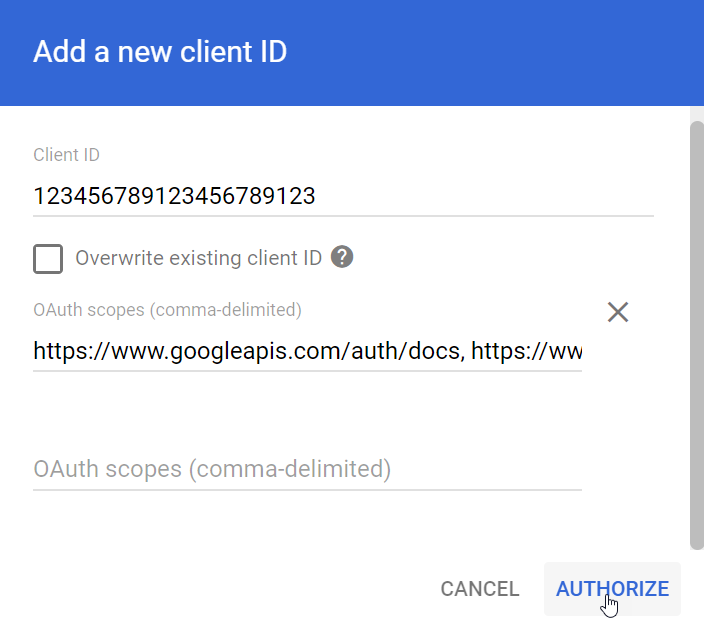
In the Add a new client ID panel, configure your new API client.
-
Enter the Client ID associated with your project’s service account.
NoteYou can get your project’s client ID from the project’s service account page of the Google Cloud Console.
-
Copy the list of comma-delimited scopes below and paste it into the OAuth scopes field.
https://www.googleapis.com/auth/drive.readonly, https://www.googleapis.com/auth/userinfo.email, https://www.googleapis.com/auth/admin.directory.user.readonly, https://www.googleapis.com/auth/admin.directory.group.readonly -
Click Authorize. The new client ID appears at the top of the API clients list.
-