Coveo, Microsoft Dynamics 365, and Security
Coveo, Microsoft Dynamics 365, and Security
Coveo uses a permission model capable of replicating any flexible security model to make sure that your data is at least as secure in your Coveo index as it’s in Microsoft Dynamics 365. Whether they’re browsing content directly in Microsoft Dynamics 365 or searching it with Coveo, your users have access to the same items, as items not matching a user’s permissions aren’t included in their search results. Therefore, they can’t use Coveo to access sensitive information that they’re not supposed to see, such as coworkers' expense accounts or confidential information handled by other teams. See Coveo management of security identities and item permissions for details.
Item Permission Model
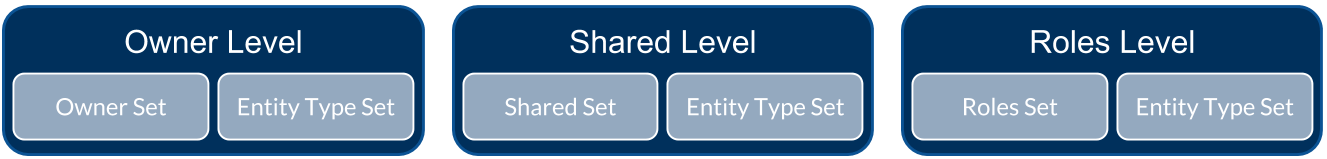
Coveo applies a permission model to each indexed item depending on the repository security model. In Microsoft Dynamics 365, this model is composed of three permission levels:
Each of these levels includes two permission sets of allowed groups or users:
-
[Level] Set: groups or users who have access to the item.
-
Entity Type Set: groups or users who typically have access to this entity type.
|
|
Note
In Microsoft Dynamics 365, the concept of denied user, that is, a user that’s explicitly forbidden to access an item, doesn’t exist. Users are either allowed to access an item or unknown to the item permission model. |
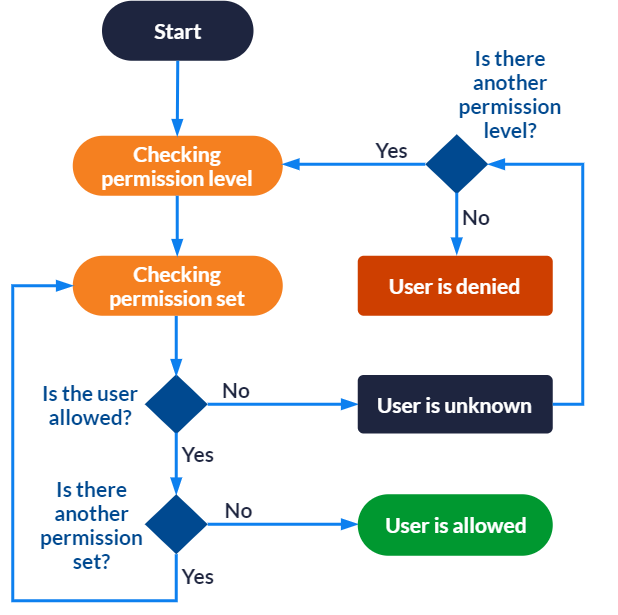
To resolve the permission model of an item and determine whether it can appear in the search results for a specific user, Coveo analyzes the item permissions as follows:
-
For each permission level, Coveo goes through each permission set:
-
If the user is allowed to access the item in all sets, the user can see the item.
-
Other permission levels are ignored.
-
If the user is unknown in some or all sets, the next permission level is checked.
-
If the user is unknown in all permission levels, the user can’t see the item.
-
Security Expansion
In order for Coveo to recognize users from Microsoft Dynamics 365, each group and user must be associated to a security identity represented by their primary email, which is then used to determine whether a user can access an item. These identities are stored in the Coveo security identity cache. At query time, the item permissions are compared to the identity in the cache to determine whether the user is allowed to access the item.
Once a day, Coveo refers to the Microsoft Dynamics 365 security provider to update the association of groups and users to their emails. Therefore, any change made to the security groups or users in Dynamics 365 will be effective in Coveo at most 24 hours later. If you want your changes to be effective immediately, you can manually launch a security identity refresh.