Navigate the Privileges tab
Navigate the Privileges tab
If you have permission to create or edit member groups, you can access the Privileges tab to manage the privileges granted to a member group.
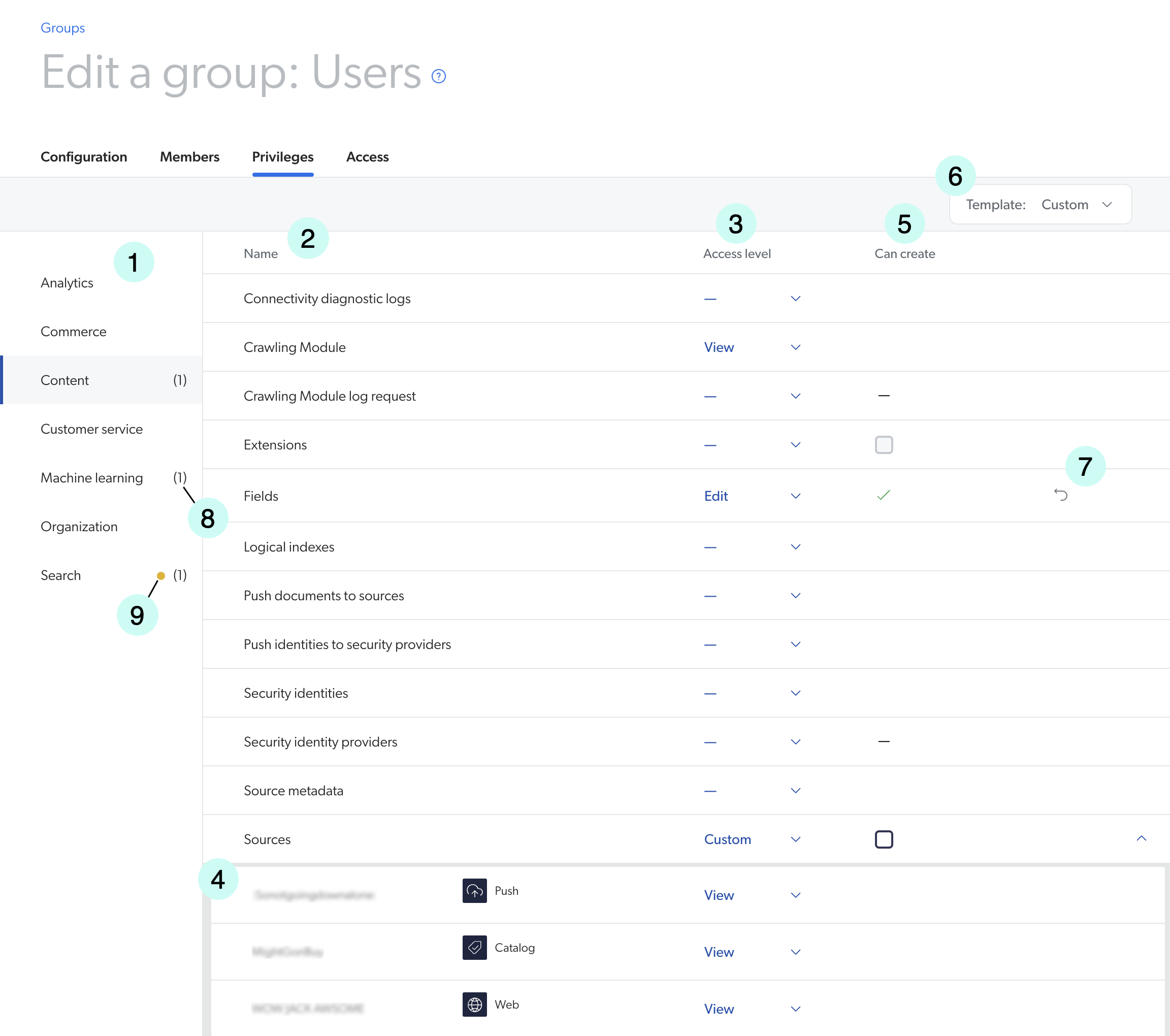
1 |
List of services |
2 |
List of domains |
3 |
Access Level column |
4 |
List of resources |
5 |
Can Create ability |
6 |
|
7 |
Discard changes button |
8 |
Unsaved changes indicator |
9 |
Warning indicator |
|
|
Notes
|
Example
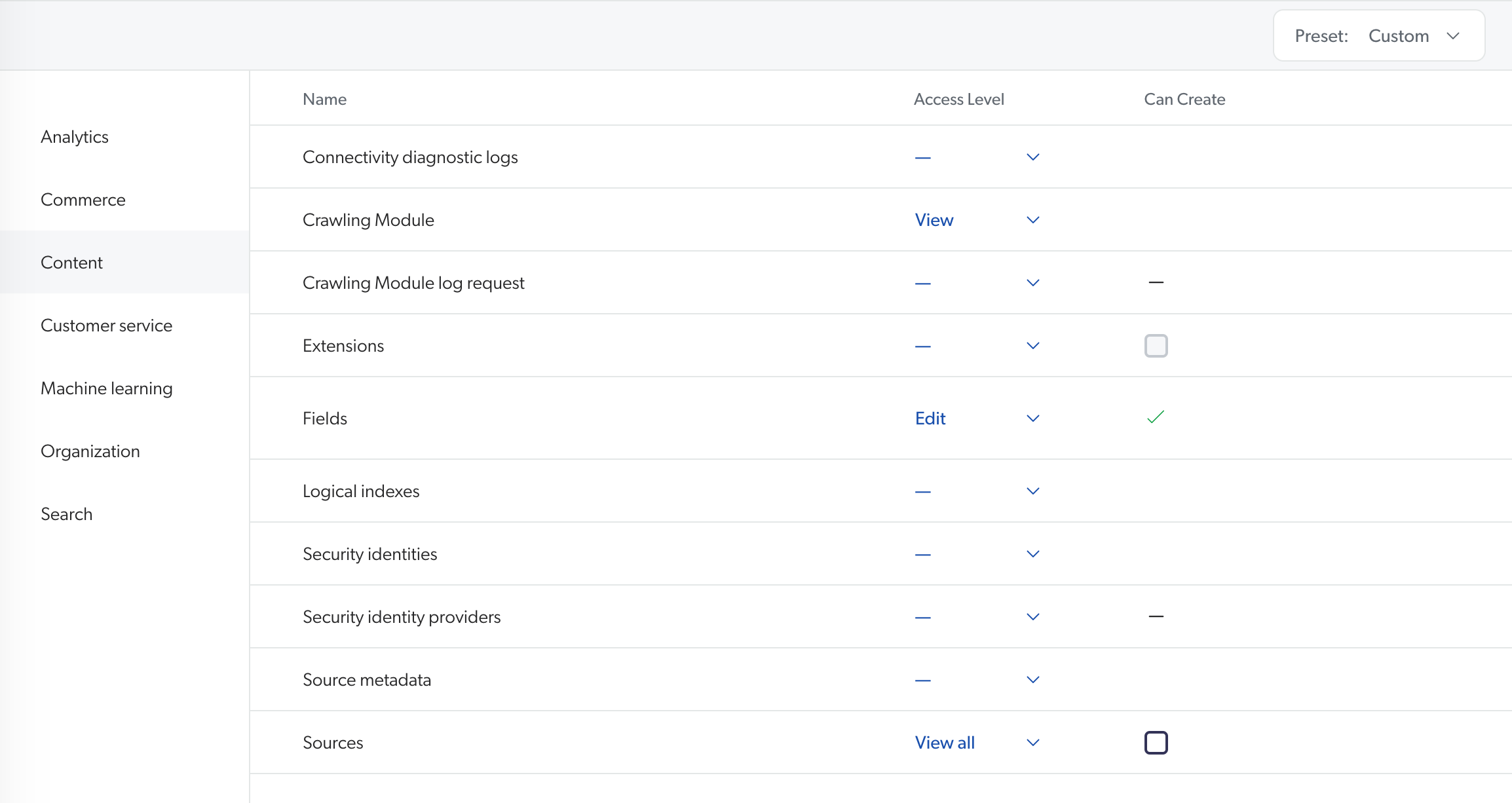
The following example shows the potential effects of varying access levels on the Coveo Administration Console. The access levels assigned to a member group are as follows:
-
The Extensions domain isn’t assigned any access level.
-
The Sources domain is set to View all.
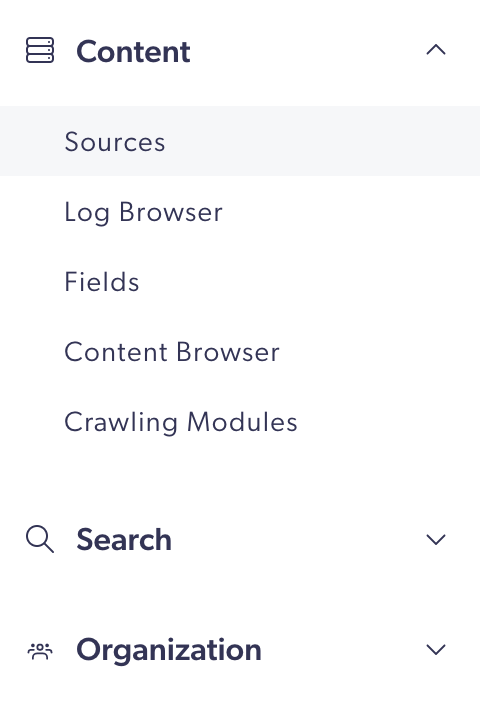
As a result, the Extensions page isn’t visible in the navigation menu for a member of this group.
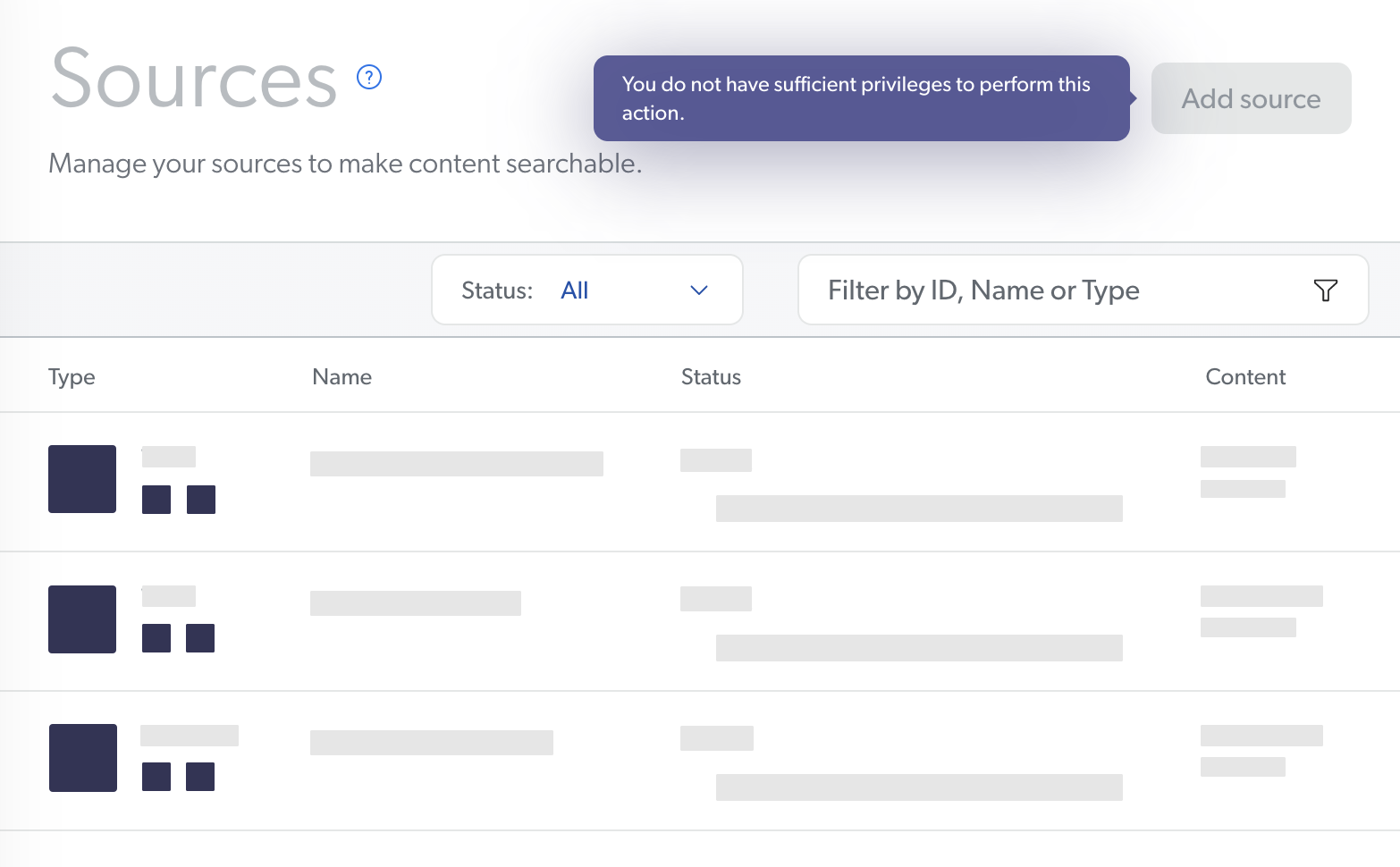
On the Sources page, members can review source configurations but not edit them. Additionally, the Add Source button is grayed out and unresponsive. When a member hovers over this button, a tooltip appears indicating that the member has insufficient privileges for adding a new source.
About the Template menu
To quickly and broadly grant privileges to a group, use the Template dropdown menu in the Privileges tab Action bar. Your selection applies to all services.
In other words, when you grant a custom access level configuration, you can save time by selecting the template configuration closest to the access level set you want to grant, and then you can edit its privileges.
The Template dropdown menu then indicates: Custom.
|
|
Note
If you don’t have all the privileges in the template you select, the missing privileges can’t be applied to the group. To fully apply a template, you must have the same or a higher access level for each domain, as the access levels you can grant depend on your own the access level. For example, if you have the privilege to view all sources, you can’t grant the Edit all or Custom access levels on the Sources domain to a group. Your only options are View all and No access. |
Template menu options
When granting privileges to a group, your options in the Template menu are:
-
Full access, which allows grantees to edit all domains. Full access is typically granted to administrators only.
-
View all, which allows grantees to see all domains of the Administration Console but forbids editing resources or creating new ones. This template can be granted to users who only have monitoring tasks.
-
Minimal access, which only grants the View access level for the Organization domain, so that users can log in to the Coveo Administration Console. You must select an access level for the desired domains to allow grantees to access the corresponding resources.
-
Six templates that correspond to the default privilege set of the built-in groups. However, this option is only available when granting privileges to a group.
-
You only want the members of a member group to be able to edit sources and fields. You select the Minimal access template, click the Content services in the menu on the left, and then select the Edit access level for Sources and Fields.
-
You want the members of a member group to be able to edit resources of the Usage Analytics, Machine Learning, and Search services, and view the resources of other services. You select the Full access template and then, for the domains of the Content and Organization services, change the access levels from Edit to View.
What’s next?
Learn about granting privileges.