Navigate the Privileges tab
Navigate the Privileges tab
When you’re allowed to create or edit member groups and/or API keys, you can access the Privileges tab, which allows you to manage the privileges granted to a member group or API key.
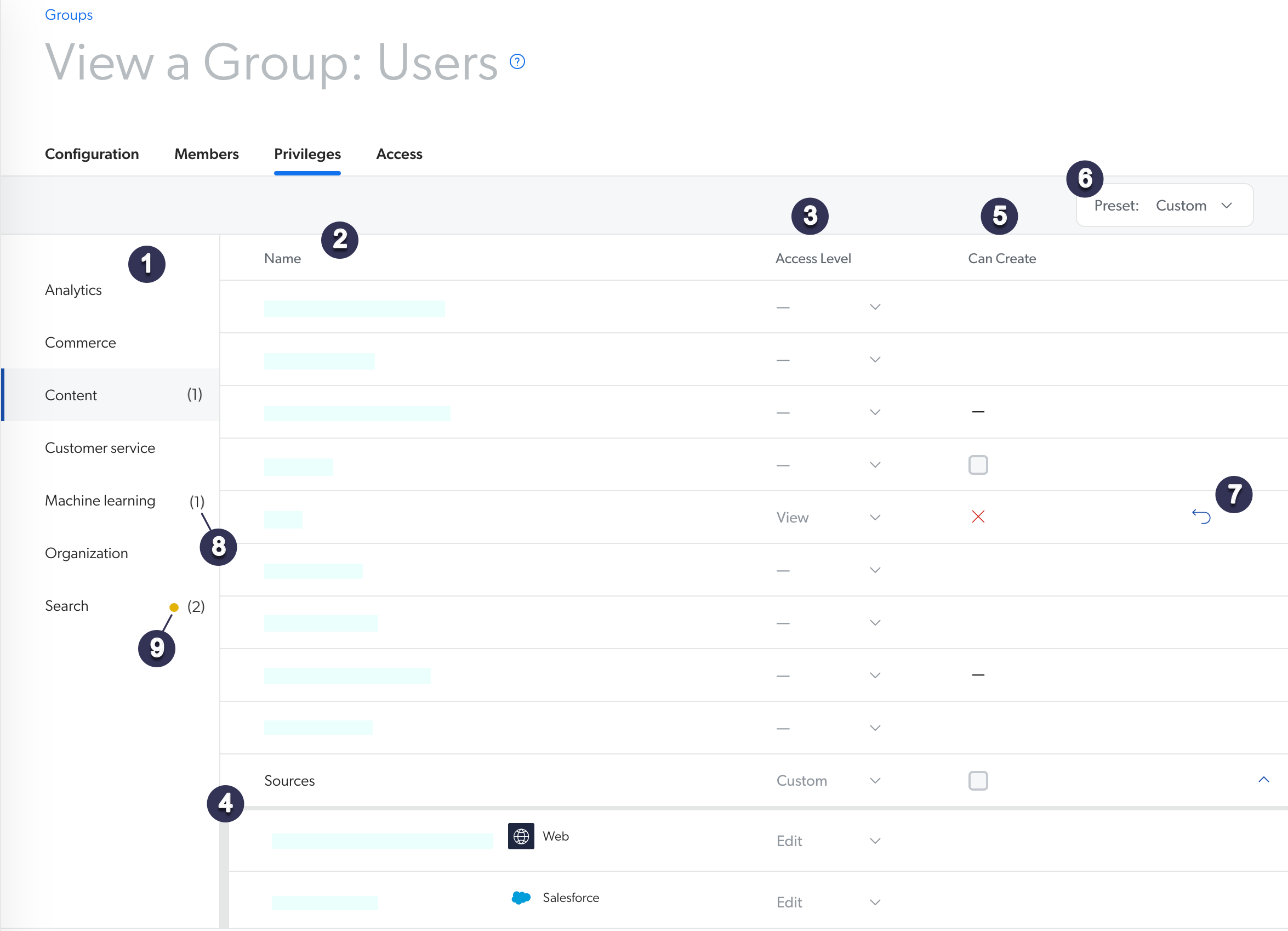
| 1 | List of services Coveo consists of several services, which each include several related domains (see Services, Domains, and Access Levels). In the Coveo Administration Console, each section of the navigation menu corresponds to a service. |
| 2 | List of domains Domains in the selected service. |
| 3 |
Access Level column Each Access Level dropdown menu contains a list of your access level options. Users or API keys with the No access (dash) access level can't access or use the corresponding features of Coveo. |
| 4 | List of resources When you select the Custom option offered for some domains, a list of the resources in this domain appears, allowing you to select an access level for each source individually. |
| 5 |
Can Create ability See Can Create Ability Dependence. |
| 6 | Preset menu See About the Preset Menu. |
| 7 | Discard changes button Clicking this button discards all changes made on a domain. |
| 8 | Unsaved changes indicator You made changes on n domains in the corresponding service. These changes will apply once you click Save. |
| 9 | Warning indicator Your changes are subject to a warning. You're encouraged to review the Privilege reference documentation before saving. |
|
|
Notes
|
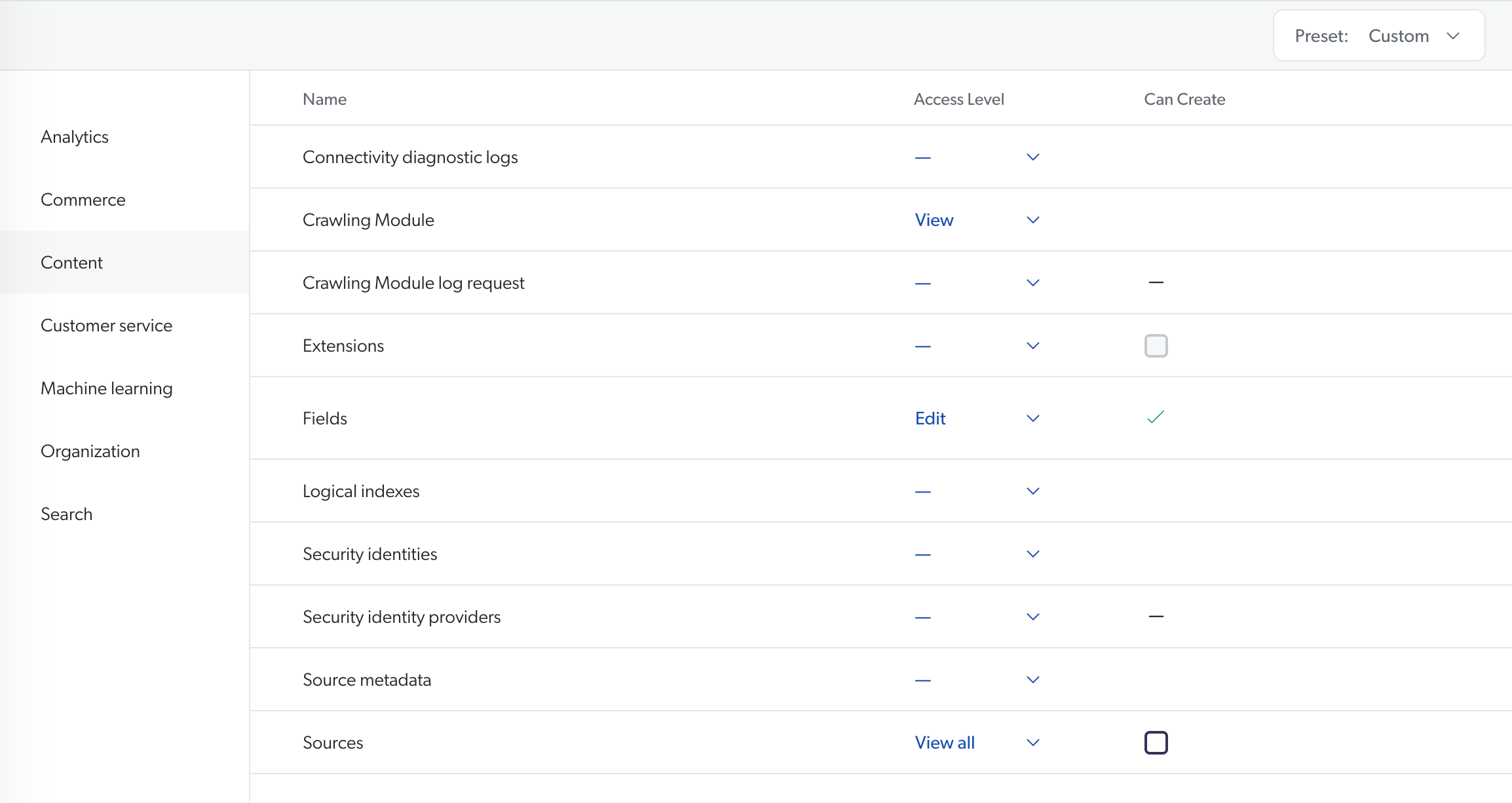
The following shows the potential effects of varying access levels on the Coveo Administration Console. Note the following access levels assigned to a member group:
-
The Extensions domain is not assigned any access level.
-
The Sources domain is set to View all.
For a member of this member group, as a result, the Extensions page isn’t visible in the navigation menu.
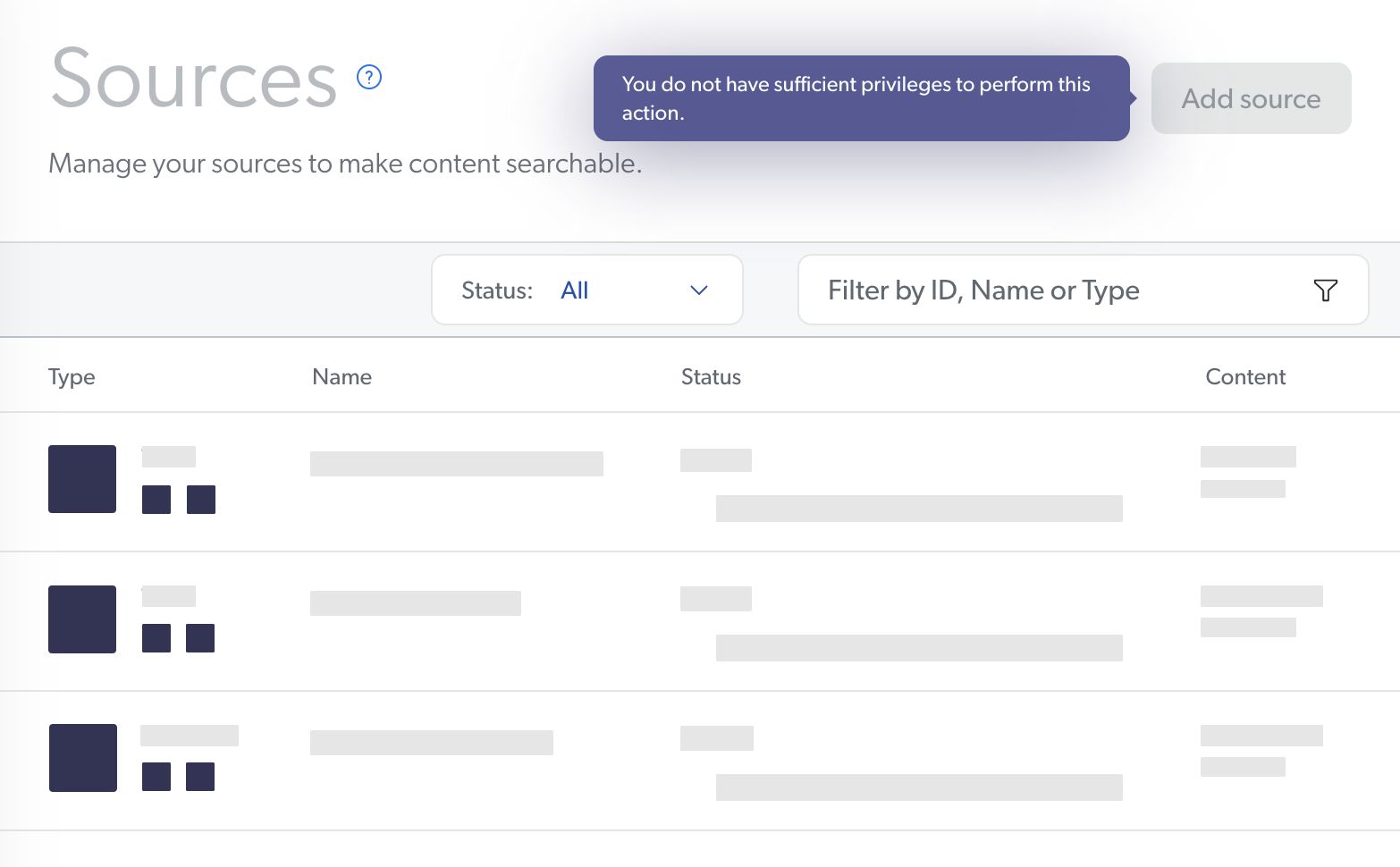
On the Sources page, source configurations can be reviewed, but not edited. The Add Source button is also grayed out and unresponsive. If the member hovers over this button, a tooltip appears indicating the member’s insufficient privileges for adding a new source.
About the Preset menu
To quickly and broadly grant privileges to a group or API key, you can use the Preset dropdown menu in the Privileges tab Action bar. Your selection applies to all services.
In other words, when granting a custom access level configuration, you can save time by selecting the preset configuration closest to the access level set you want to grant, and then editing the desired privileges.
The Preset dropdown menu then indicates: Custom.
|
|
Note
If you don’t have all the privileges in the preset you select, the missing privileges can’t be applied to the group. To fully apply a preset, you must have the same or a higher access level for each domain, as the access levels you can grant depend on the access level you have yourself. For example, if you have the privilege to view all sources, you can’t grant the Edit all or Custom access levels on the Sources domain to an API key or group. Your only options are therefore View all and No access. |
Preset menu for member groups
When granting privileges to a group, your options in the Preset menu are:
-
Full access, which allows grantees to edit all domains. Full access is typically granted to administrators only.
-
View all, which allows grantees to see all domains of the Administration Console but forbids to edit resources or create new ones. This preset can be granted to users that only have monitoring tasks.
-
Minimal access, which only grants the View access level for the Organization domain, so that users can log in to the Coveo Administration Console. You must then select an access level for the desired domains to allow grantees to access the corresponding resources.
-
Six templates corresponding to the default privilege set of the built-in groups. This option is however only available when granting privileges to a group.
-
You want the members of a member group to only be able to edit sources and fields. You therefore select the Minimal access preset configuration, click the Content services in the menu on the left, and then select the Edit access level for Sources and Fields.
-
You want the members of a member group to be able to edit resources of the Usage Analytics, Machine Learning, and Search services and view the resources of other services. You therefore select the Full access preset configuration and then, for the domains of the Content and Organization services, change the access levels from Edit to View.
Preset menu for API keys
When granting privileges to an API key, your options in the Preset menu are:
| Preset | Description | Grant to |
|---|---|---|
Minimal access |
Doesn’t grant any privileges. You can use it as a starting point to grant your API key only the privileges needed |
Any API key |
Admin |
Allows making administrative changes to your Coveo organization just like you would in the Administration Console. This preset is useful if you’re building an application that needs to modify your organization. |
Private (server-side) API keys only |
Search |
Allows passing the user’s identity to Coveo along with their query, so Coveo can return the items they’re allowed to see. Items with a permission model may appear in the search results, depending on whether a user is allowed to see each item. |
Private (server-side) API keys only |
Anonymous search |
Doesn’t pass the user’s identity to Coveo along with their identity. Users aren’t required to log in to use the interface, therefore they’re all anonymous. Items with a permission model don’t appear in the search results. |
API key in a public search interface (users aren’t authenticated) |
Monitoring |
Grants the View access level on most domains. It’s useful if you’re building external statistics dashboards for your Coveo organization, for example. |
Private (server-side) API keys only |
Analytics |
Grants the privilege to send usage data to your Coveo organization using any identity. It’s useful if you’re building external statistics dashboards for your Coveo organization, for example. |
API key in a search interface (users may or may not be authenticated) |
What’s next?
Learn about granting privileges.